Let's solve challenges - Cellebrite 2022 CTF Writeup

I had the pleasure of playing Cellebrite's new CTF last week, which kept me entertained in the evenings.
Unfortunately, I didn't have much time to devote to it, but I believe it was very useful for both reviewing old concepts and learning new ones.
The following tools was used during the challenge:
- X-Ways Forensics (http://www.x-ways.net/forensics/)
- Cellebrite PA (https://cellebrite.com/en/physical-analyzer/)
- Cellebrite Inspector (https://cellebrite.com/en/inspector/)
- iLEAPP (https://github.com/abrignoni/iLEAPP)
- ALEAPP (https://github.com/abrignoni/ALEAPP)
- Eric Zimmerman's tools (https://ericzimmerman.github.io/#!index.md)
- Arsenal Image Mounter (https://arsenalrecon.com/products/)
- WINHELLO2hashcat (https://github.com/Banaanhangwagen/WINHELLO2hashcat)
I will not follow the order of the devices as indicated in the challenge!!

---Marsha’s PC---
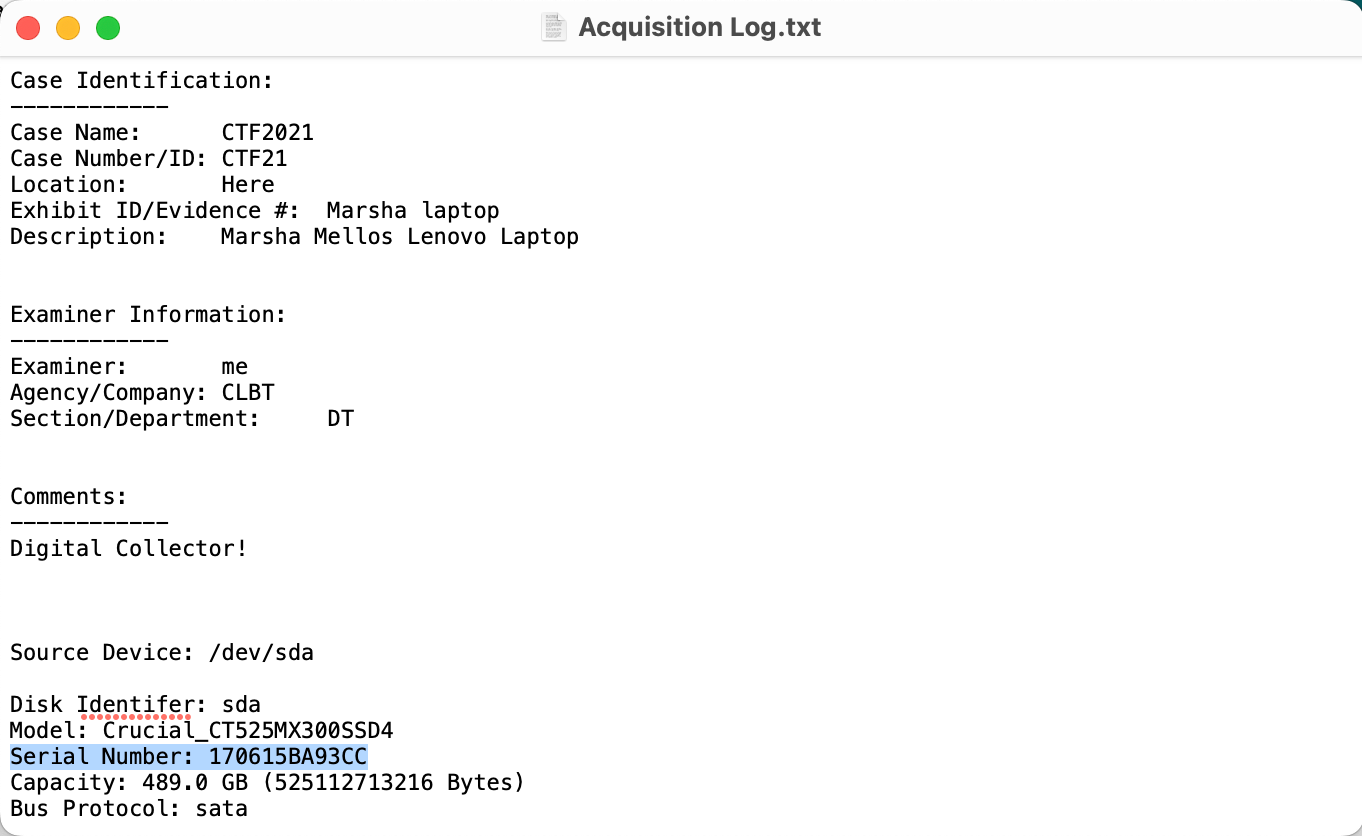
Question #1: What is the Serial Number of the disk acquired?
Flag: 170615BA93CC
There are several ways to answer this question (including using Windows Event Logs), but I believe the quickest method is to go to the acquisition log file and look for the information.
---
Question #2: How did the user most recently sign into Windows?
Flag: Fingerprint
The answer to the question is found in the registry key "LogonUI" (SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI), specifically in the value name "LastLoggedOnProvider". After analyzing the current users (marsh) we can see the value {BEC09223-B018-416D-A0AC-523971B639F5} that corresponds to the fingerprint methodology.
---
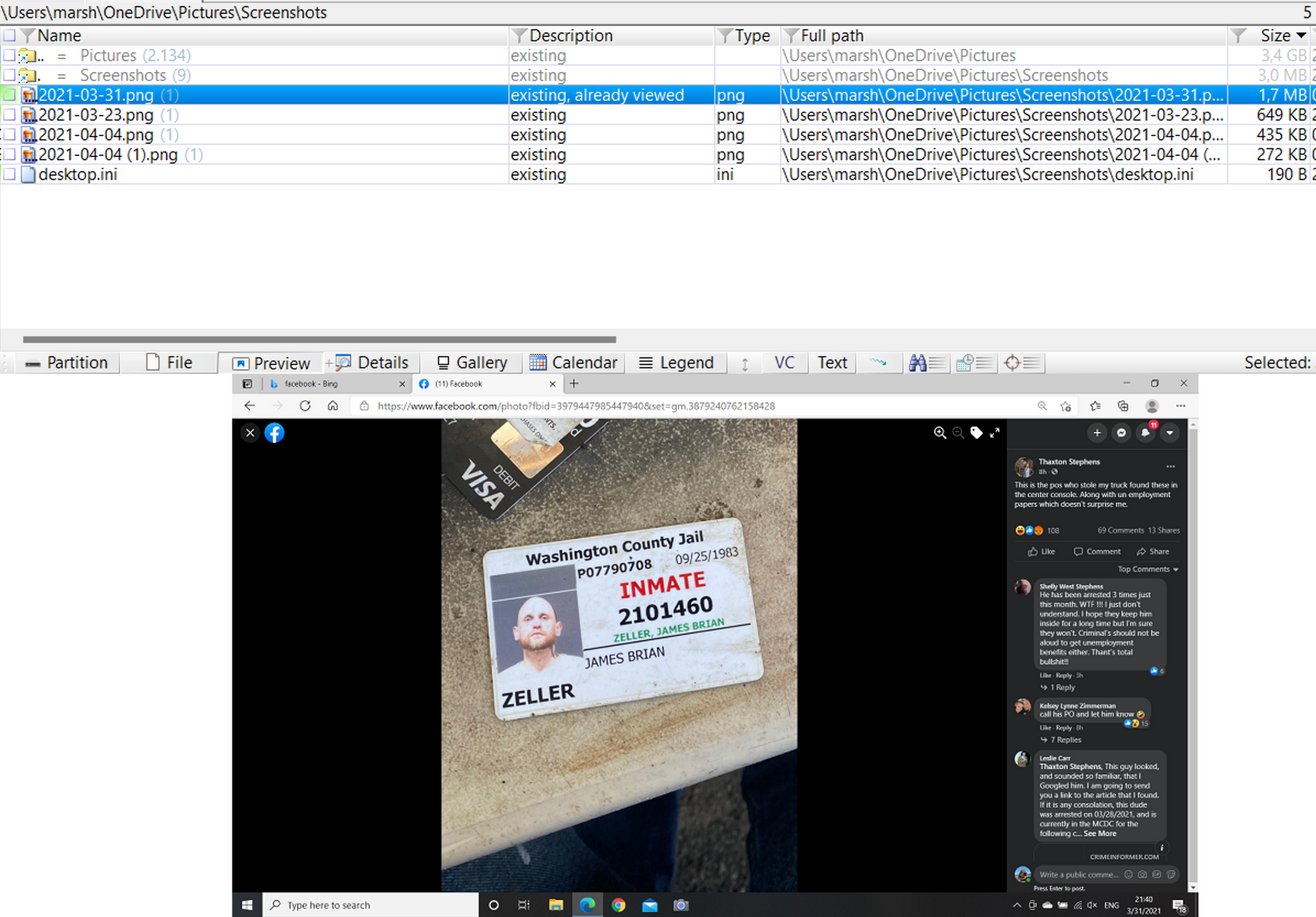
Question #3: Someone stole a truck and left his inmate card behind. What is his inmate number?
Flag: 2101460
This question was not difficult to answer. My approach was to use X-Ways to navigate the forensic image in order to filter all of the images, and after further filtering by size greater than 600kb, I was able to identify the image of interest located in "Users/marsh/OneDrive/Pictures/Screenshots/" folder.
---
Question #4: What is the serial number of the last USB drive connected to the device, excluding acquisition tools?
Flag: ...I'm curious to know too...🥲
This was deceptively easy. I simply used Inspector's "Actionable Intel" to analyze and sort all connected USBs by date of last disconnection. The answers given appeared to be incorrect, but at a certain point they become correct. We'll wait for the official writeup :)
---
Question #5: What is the only camera model that was found within a pictured created by the user browsing the Internet?
Flag: Canon EOS 5D Mark II
X-Ways Forensics was once again our best friend. It was sufficient, in this case, to use the "Refine Volume Snapshot" function to analyze all of the metadata present in the images and then filtering for the Metadata field. The "Canon EOS 5D Mark II" is the only camera model available.
---
Question #7: What is the content of a user-made file where the file extension is a mismatch?
Flag: Huh this is a test
Always looking around inside the forensic copy, particularly inside the path "Users/marsh/Google Drive/", we can see a file named "Figure it out.zip". It's worth noting that the hex value only displays the string "Huh this is a test" and lacks the standard zip file header (and footer).
---
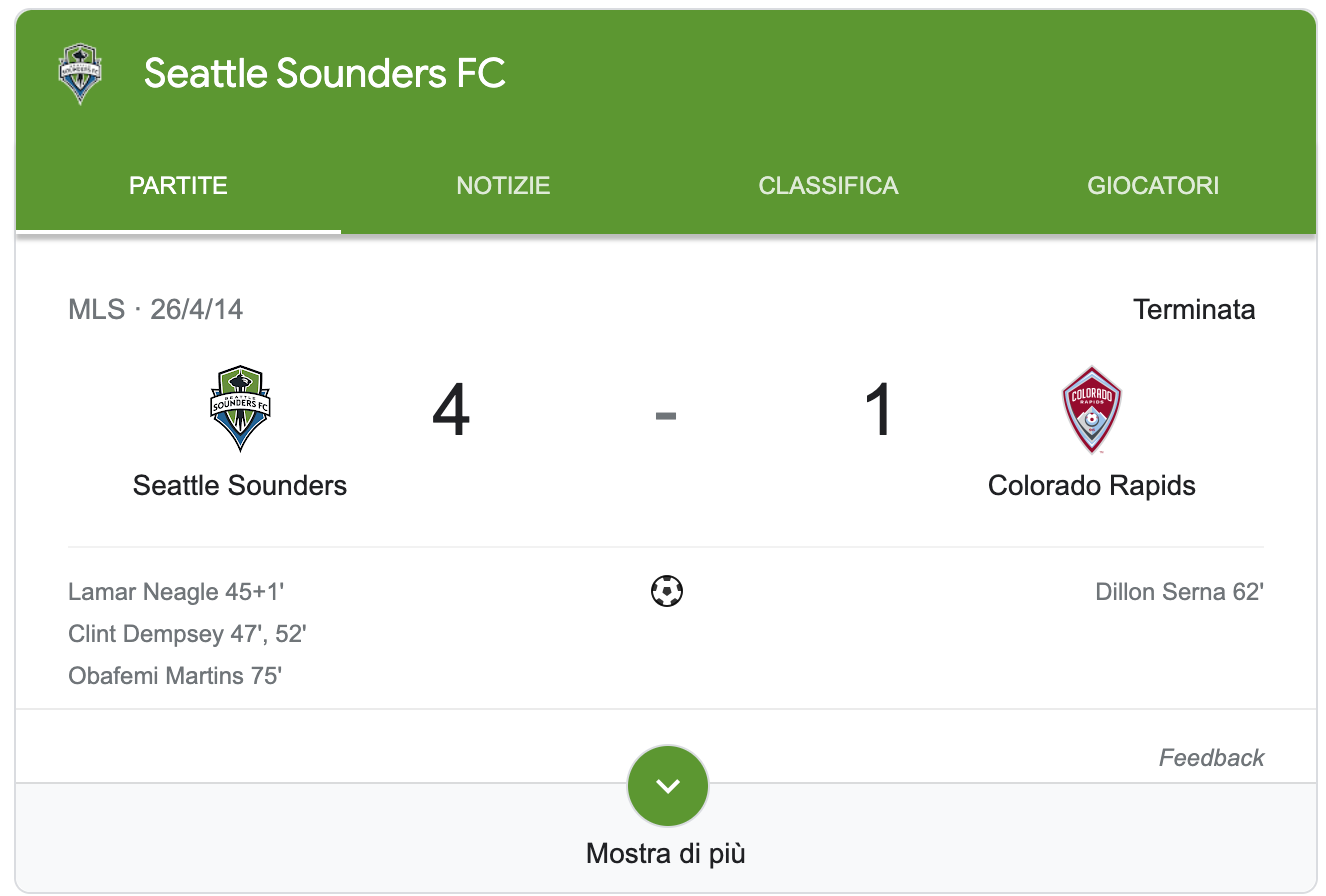
Question #8: The target captured a sports game that took place in April 2014. What was the name of the venue (at that time) and the name of the guest team? Format: [Name of stadium] [guest team] eg: Mercedes Benz Stadium Atlanta Falcons
Flag: CenturyLink Field Colorado Rapids
I had a great time here because some basic OSINT skills were required. The first step was to look for anything with the year 2014 on it. The file "20140426_205245000_iOS.MOV" was immediately identified as a video with the text "Welcome to CENTURYLINK FIELD" clearly visible. To complete the answer, it was necessary to determine which match was held on April 26, 2014: Colorado Rapids vs. Seattle Sounders
---
Question #10: What is the Windows Hello PIN code of the user signed into the Windows PC with a Microsoft account?
Flag: 134679
I used WINHELLO2hashcat to solve this challenge. I remembered this tweet
We just added support to crack Windows "Hello" PIN/Password authentication in hashcat! Regarding all technical details, please have a look at this forum thread: https://t.co/DA2py0eGZW Thanks to @tijldeneut and @banaanhangwagen for all the intense preparational work pic.twitter.com/9xG4Qfvfhu
— hashcat (@hashcat) November 15, 2021
and realized right away that this was the way to go. I used hashcat to crack the hash of interest after extracting it:
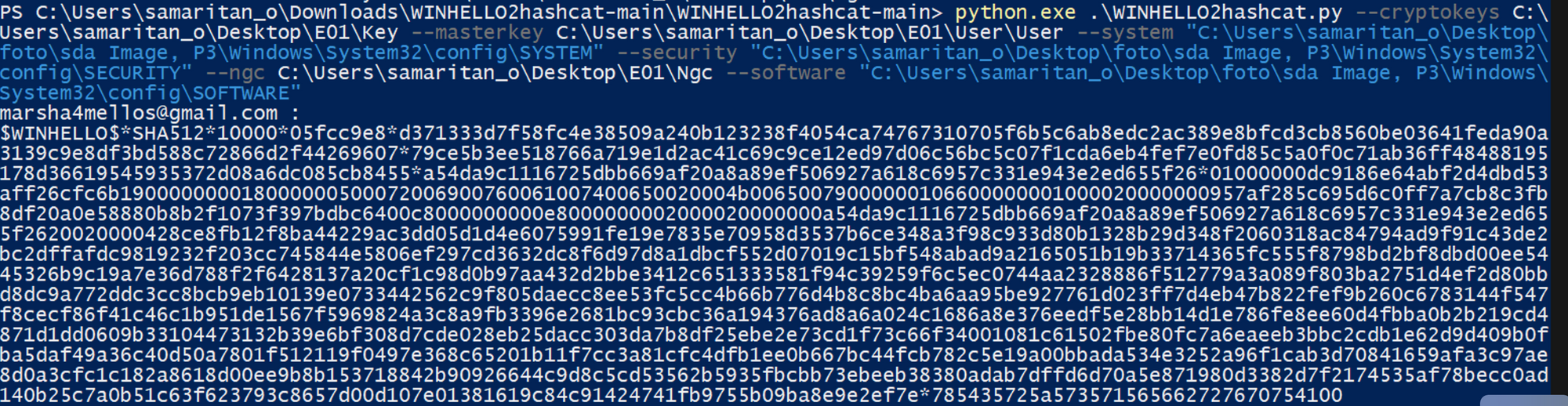
As a result, we have 134679 code.
BONUS POINT: I hadn't had a chance to look at Marsha's iPhone while working on this challenge. The password for the encrypted backup is 134679, as indicated in the "PhoneInfo.txt" file. Instead of cracking the code, it would have been possible to try this password.
---Marsha’s iPhone---
Question #44: Criminals tend to keep their business private. The suspects used an App that hides data (photos/video/contacts) behind an ordinary calculator. Provide icloud address used to purchase this app.
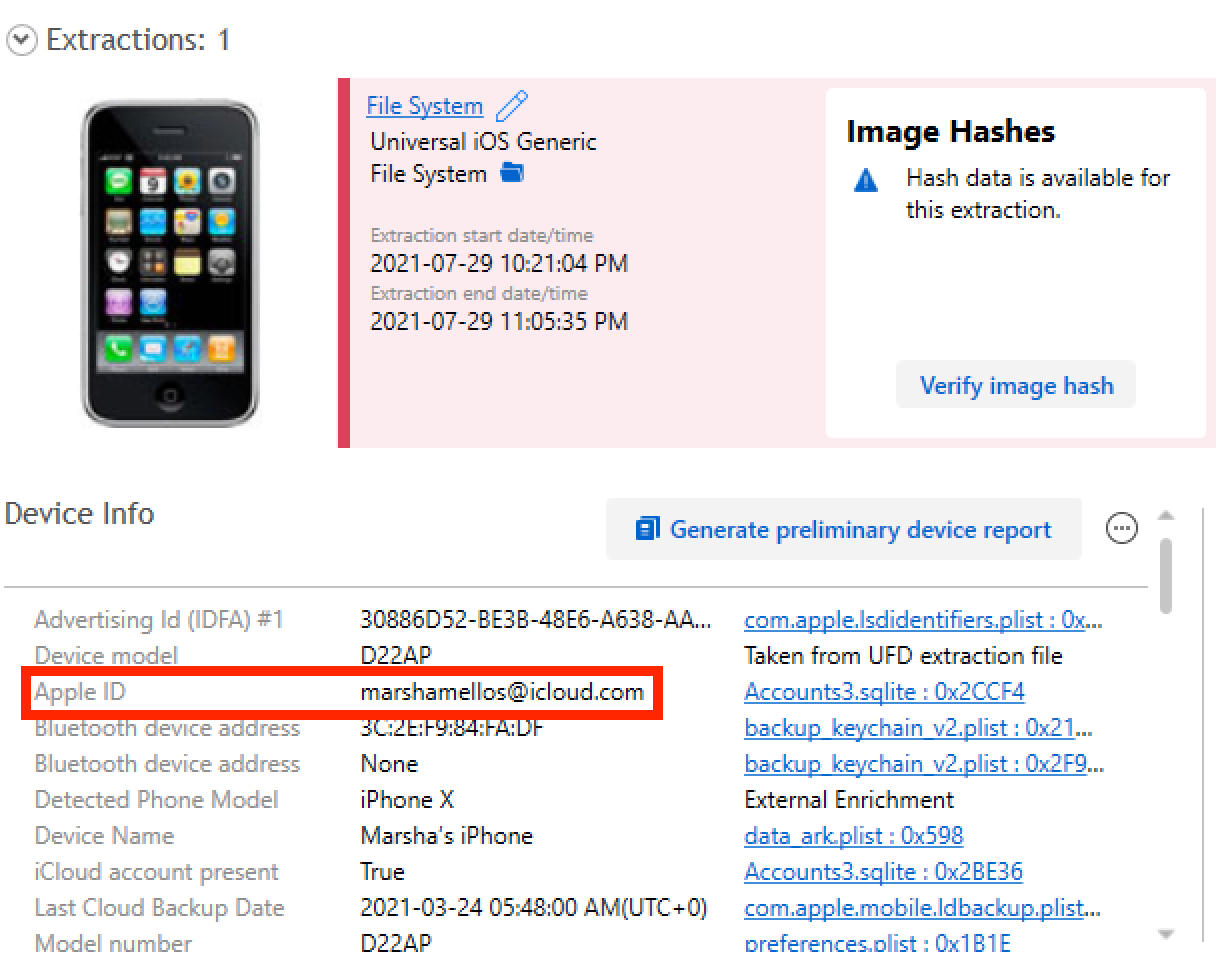
Flag: marshamellos@icloud.com
This question can be answered in a variety of ways. The simplest, in my opinion, is to locate the iCloud account that has been configured within the device. The account turns out to be marshamellos@icloud.com, as shown in the image below.
---
Question #45: What is the device vendor’s internal model name?
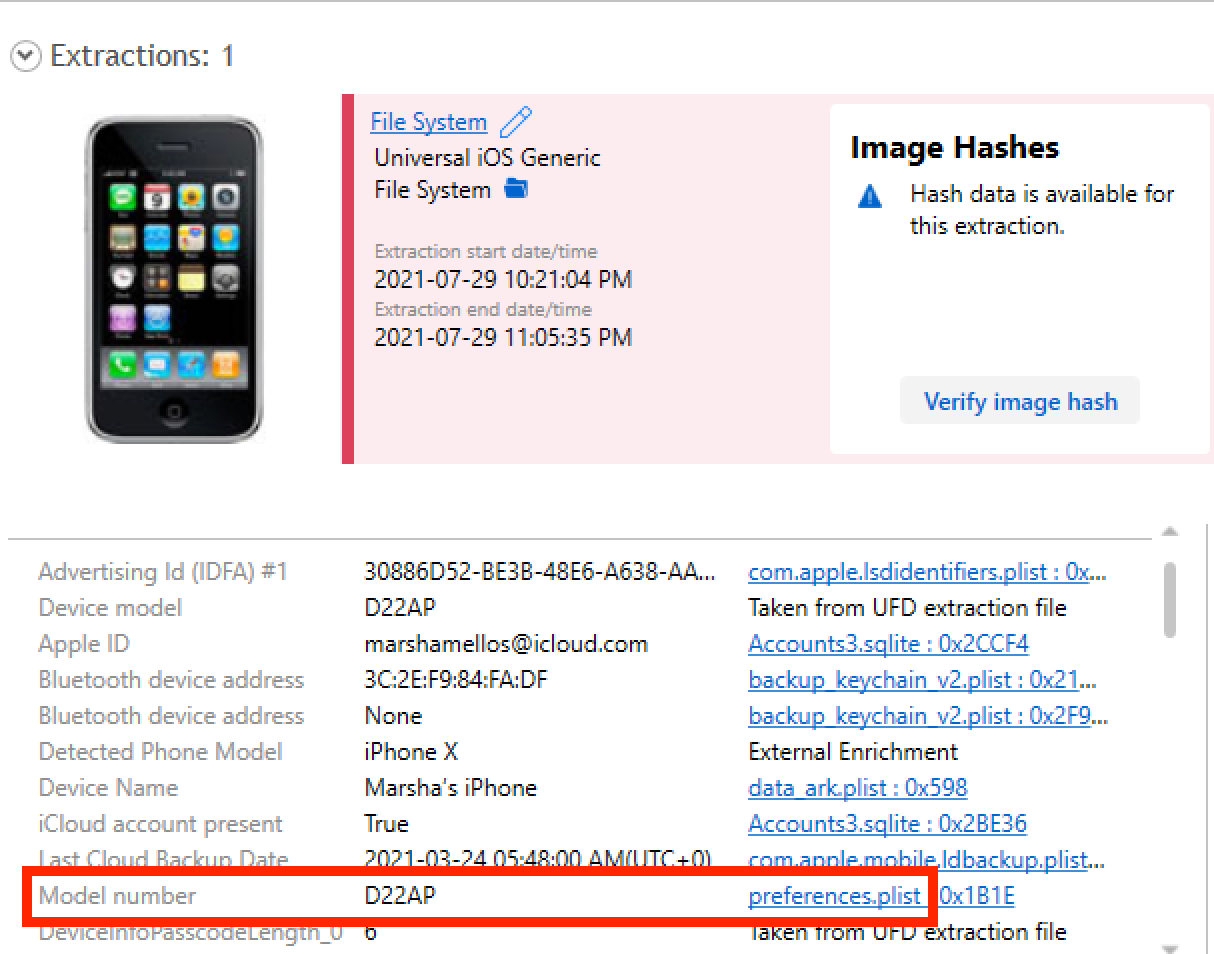
Flag: D22AP
As previously stated. This data is stored in several locations, one of which is the "preferences.plist" file.
---
Question #48: The suspect had Pizza for lunch, what was the date and time of the order? Format: MM-DD-YYYY HH:MM, e.g. 01-22-2019 19:46
Flag: 03-08-2021 12:11
It was necessary to examine the photos in the media library in order to answer this question. The image shown below can be found:

---
Question #50: What is the most frequently interacted phone number over a call? format should be +[country_code][number] for example: +97243501234
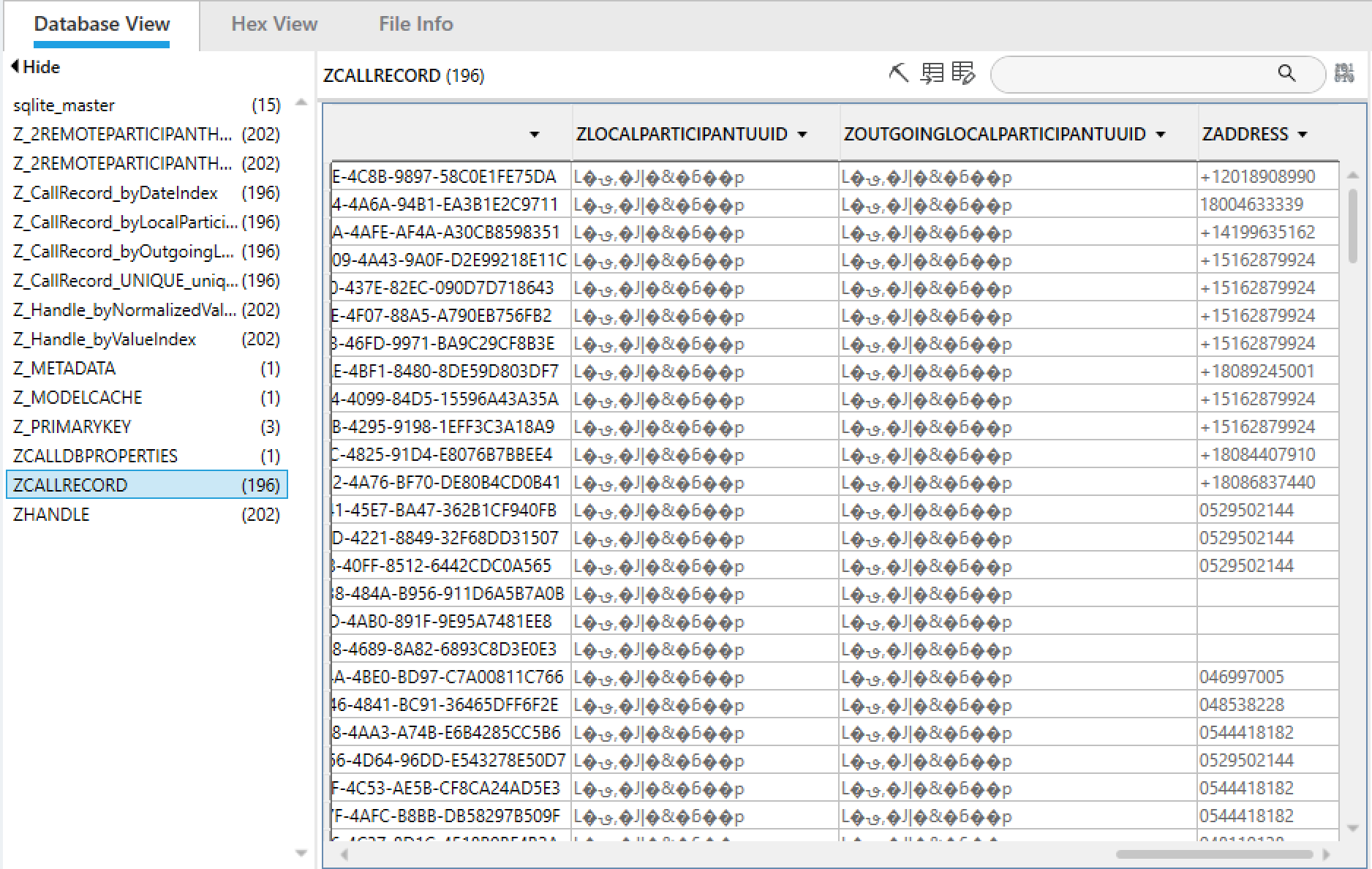
Flag: +15162879924
The simplest and most immediate solution is to use PA's "SQLite Wizard" feature to create a query that returns the number of times a phone number appears on "CallHistory.storedata" database.
---Heisenberg Android---
Question #13: What package was used by the Mobile App used by Heisenberg to scan/optimize his device? (package name)
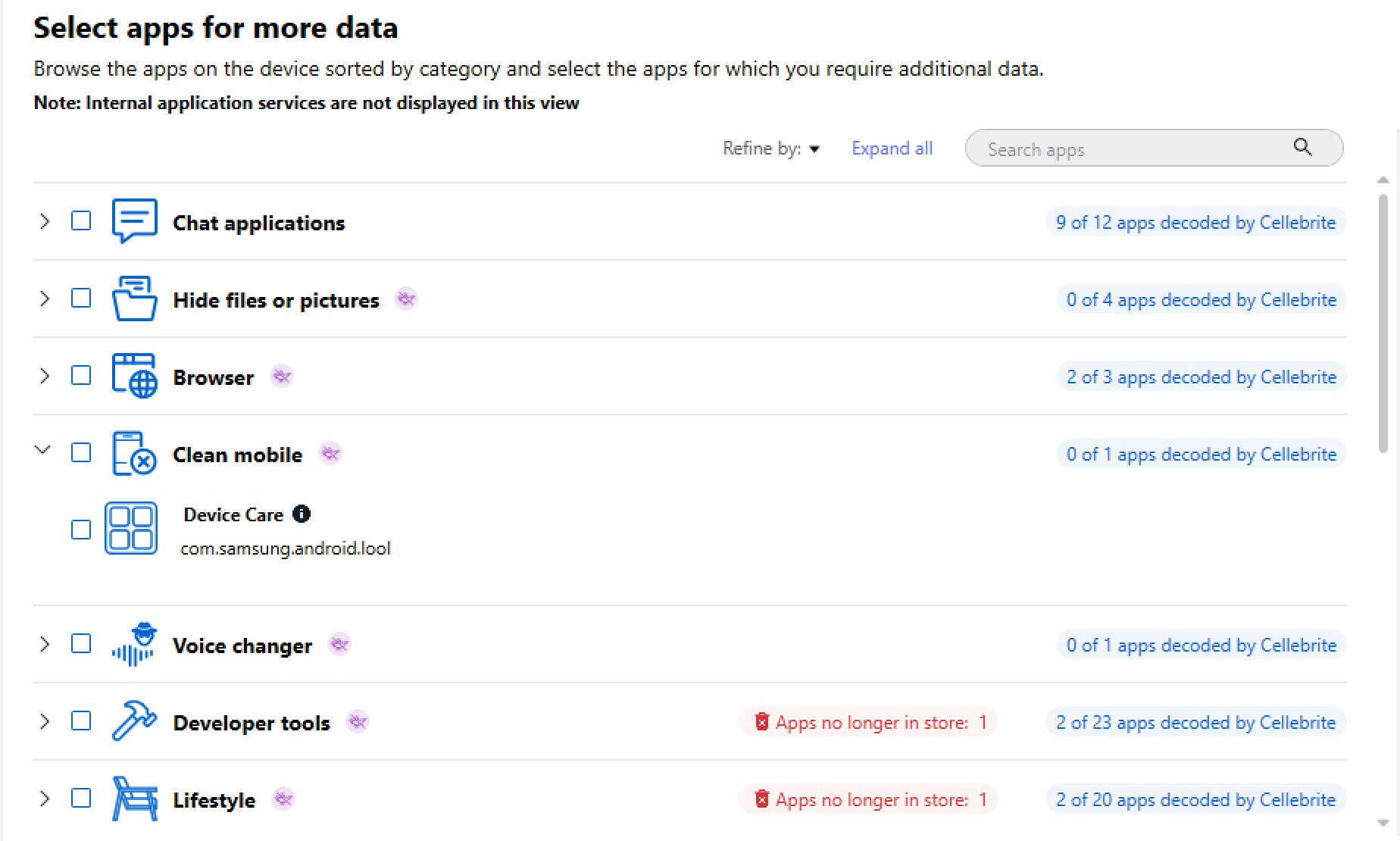
Flag: com.samsung.android.lool
The answer can be found in the "Clean Mobile" category of the PA's "Installed Application" view:
---
Question #14: What is the package name used by the Mobile App which Heisenberg looked up license plates/VIN of target vehices?
Flag: com.orto.usa
Looking over the installed applications again, I noticed that com.orto.usa has the description "Free License Plate Lookup and Vehicle VIN Report"
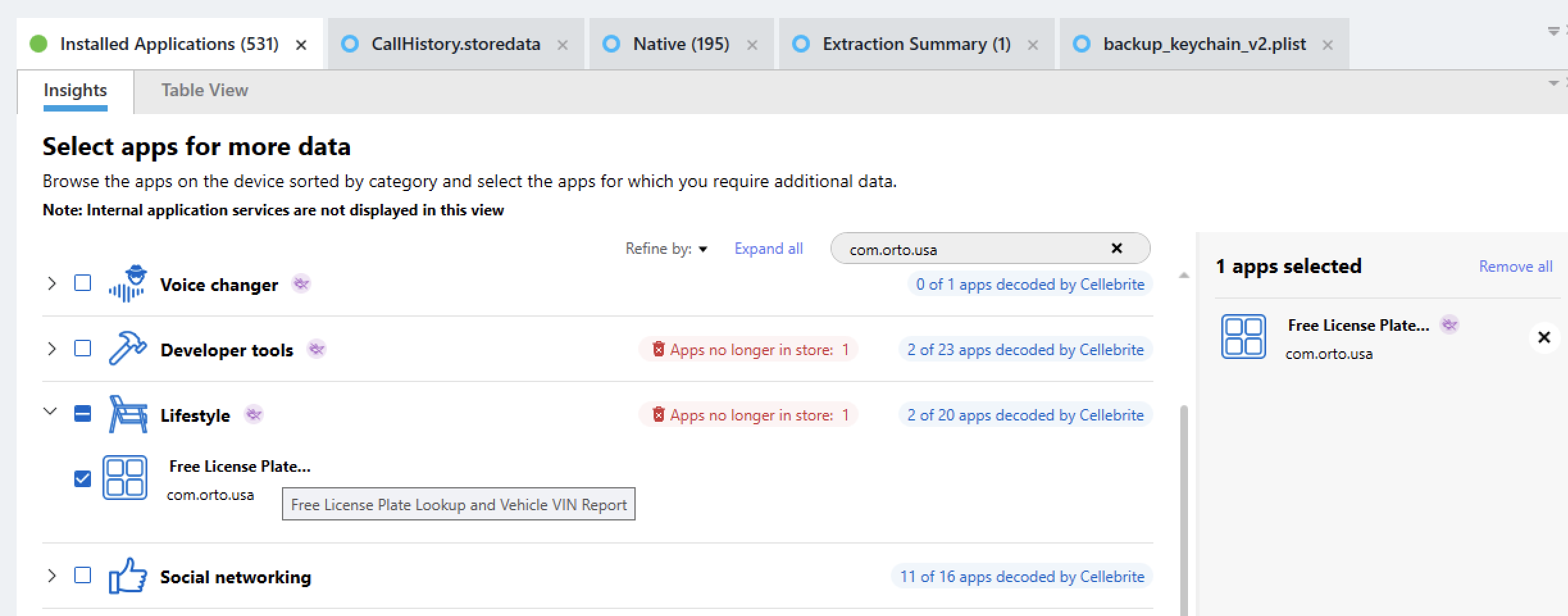
---
Question #15: What app does “zebedee.db” correspond to?
Flag: Device Health Services
Looking for the file "zebedee.db" with PA, the answer is quite simple to find:
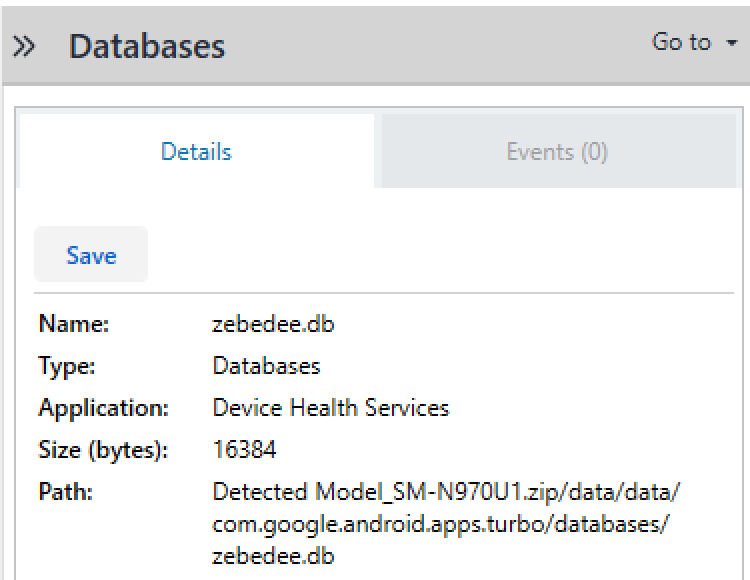
---
Question #16: What is the password for mobile data hotspot on Heisenberg’s device that was shared with Beth? (Case Sensitive)
Flag: yipz5901
The answer can be found in the "\temp\Dump\data\misc\apexdata\com.android.wifi\WifiConfigStoreSoftAp.xml" file, which contains the desired password. Alternatively, using ALEAPP it's possible to have the information already parsed:
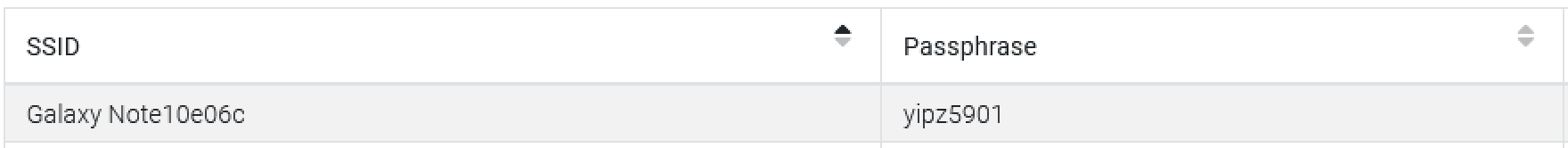
---
Question #18: What is the phone number of the undercover cop who approached Heisenberg? (Format: +1–212–555–1234)
Flag: +1–540–299–3169
In this case, knowing which number Heisenberg had exchanged the most messages with was sufficient. Furthermore, reading the chat, it is clear that the two are discussing about a Hyundai car. Once again, Cellebrite PA comes to our aid:
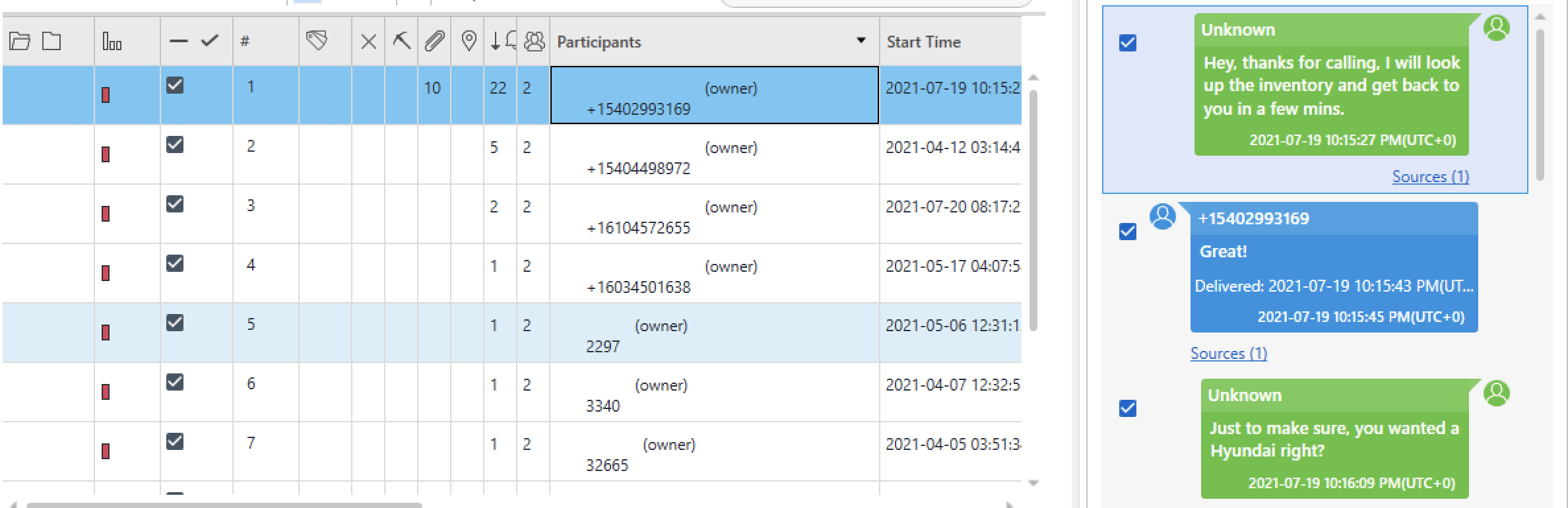
---
Question #19: BONUS Question Select anything to receive 10pts.
Flag: Correct
---
Question #21: Based on retrieved data from the device, the phone operated in West Virginia. True/False?
Flag: True
Excuse me, but I forgot to take notes for this answer, so after about 10 days, I have no idea how I arrived at the solution 🥲🥲🥲🥲🥲🥲🥲🥲🥲🥲🥲🥲🥲🥲🥲🥲🥲🥲🥲🥲
---
Question #22: How many native images on the device contain location data?
Flag: ...same situation as in question #4...
I used PA to search for images that contained geographic locations. The outcome depicted in the image below was always deemed incorrect. The answer was then revealed to be correct, as if by magic:
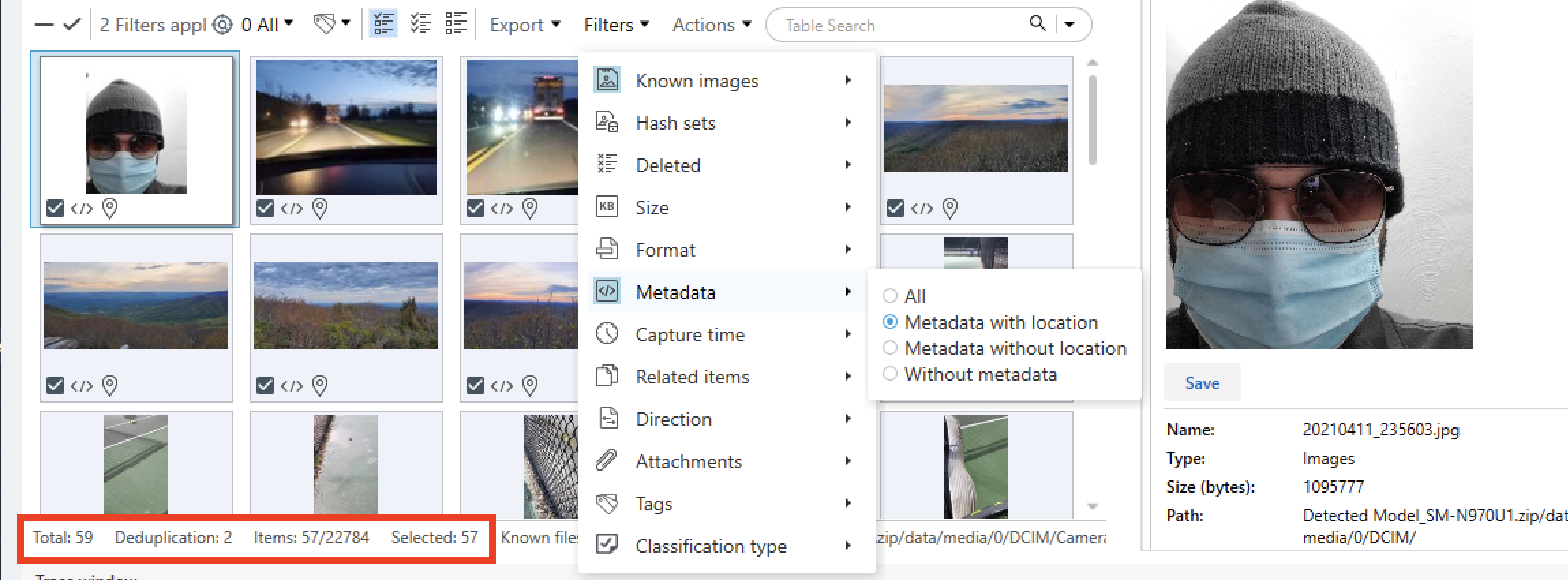
---
Question #23: What is the IMSI of the device?
Flag: 310260275793897
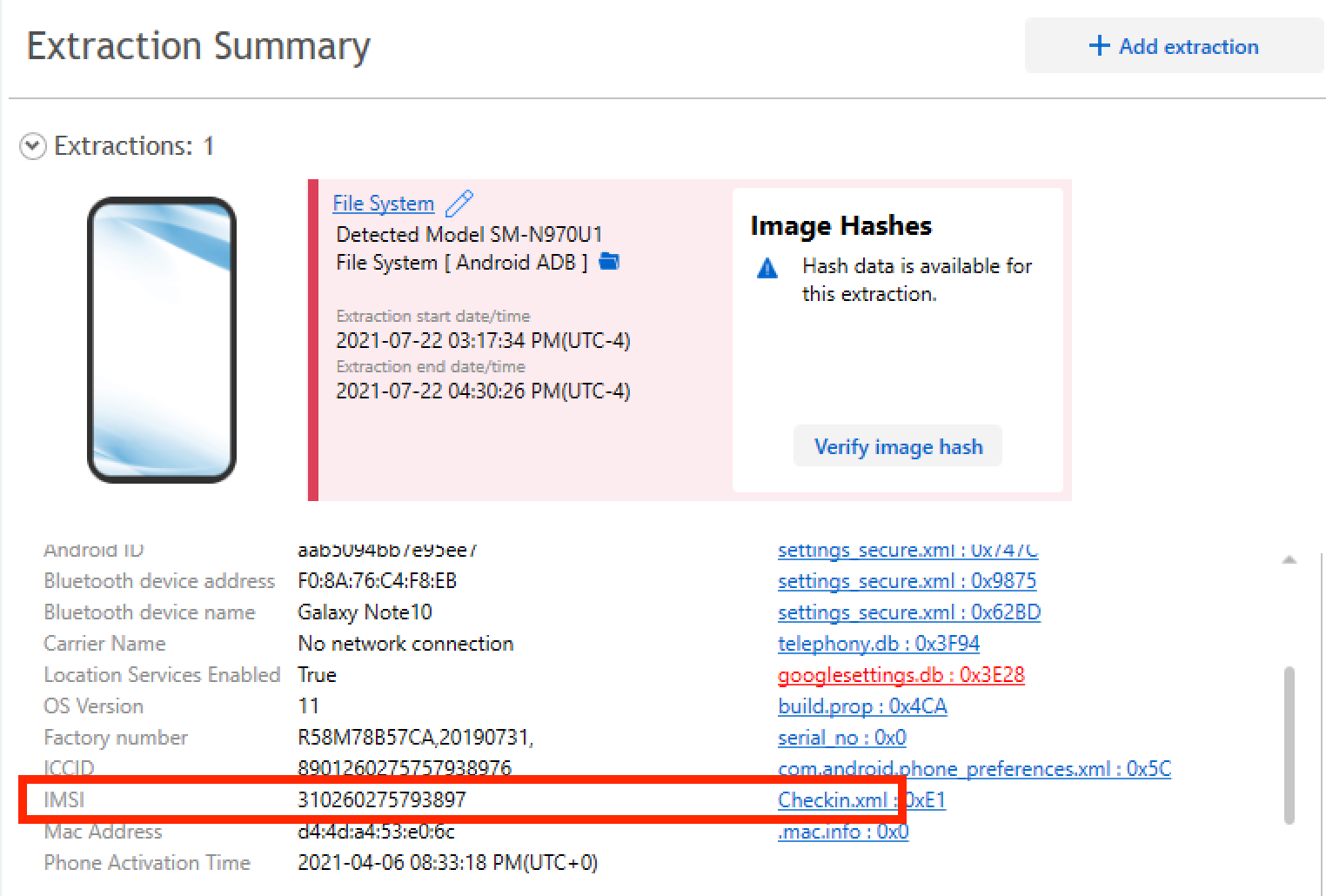
---
Question #24: Was the image with the MD5 hash “066858f4b1971b0501b9a06296936a34” hidden by Heisenberg? If Yes, what is the name of the package of the app used to hide the image else answer No. Example: yes+com.apple.wallet
Flag: yes+com.flatfish.cal.privacy
To answer this question, I searched in PA for the specific hash and, after reading the results, I discovered that the image was located within the application "com.flatfish.cal.privacy":
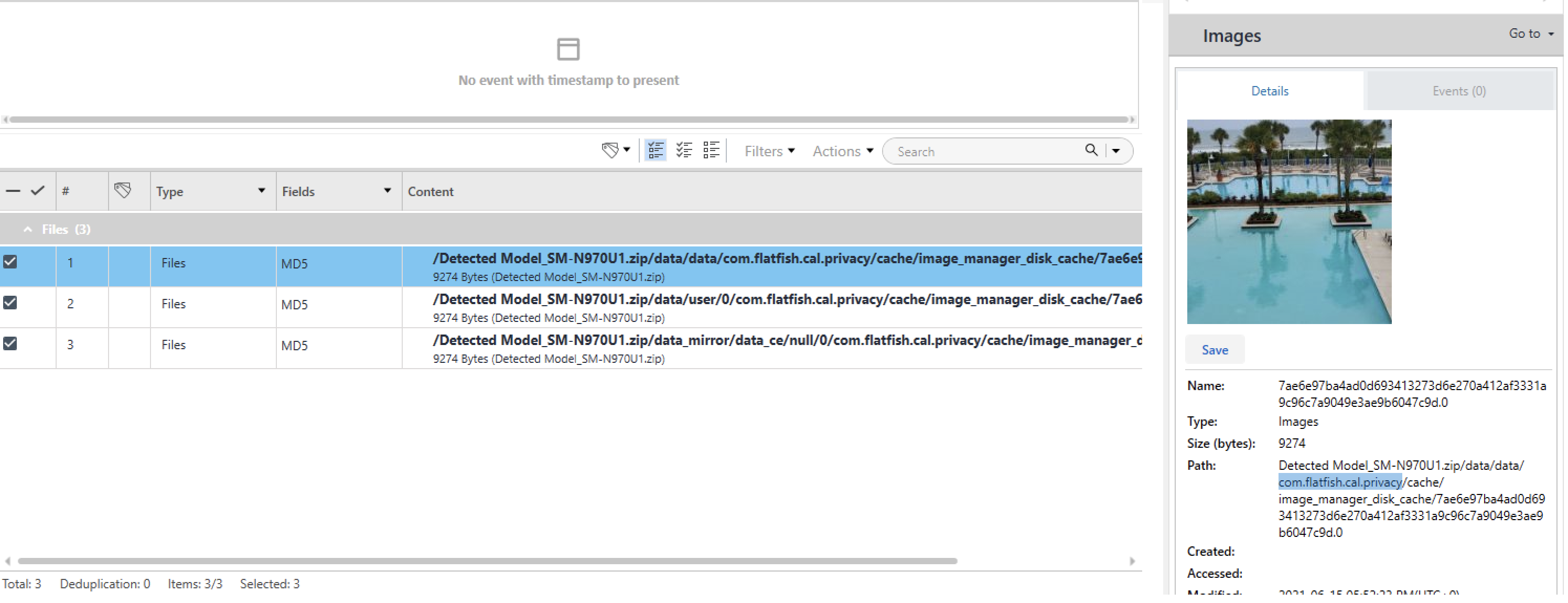
---Beth iOS---
Question #31: Beth wanted to meet her partner in an isolated place in the mountains to close a deal. Which email address did she send to?
Flag: livingstonhank11@gmail.com
In this case, I searched for the keyword "mountain" in PA and found an email sent to the address "livingstonhank11@gmail.com" among the results:
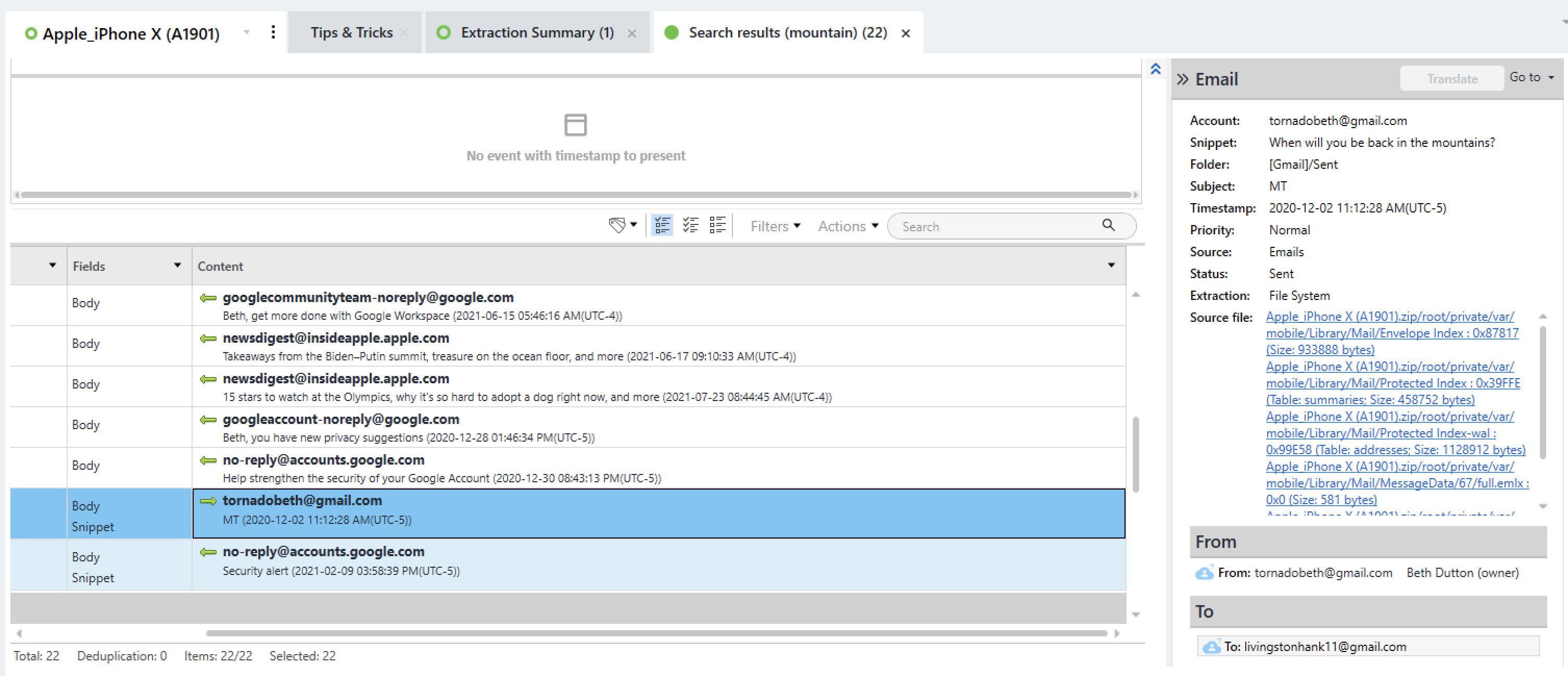
---
Question #32: Where was Beth on June 29th 2021 when she made a call to Marsha? (Provide only the city in your answer)
Flag: New York
This was a very nice question to answer. As a first step, I attempted to filter the dates of interest in PA to discover that the phone registered a position in close proximity to the highlighted call. The coordinates discovered are (40.721600, -73.957700), which, when searched on Maps, immediately lead me to the conclusion that the city is New York.
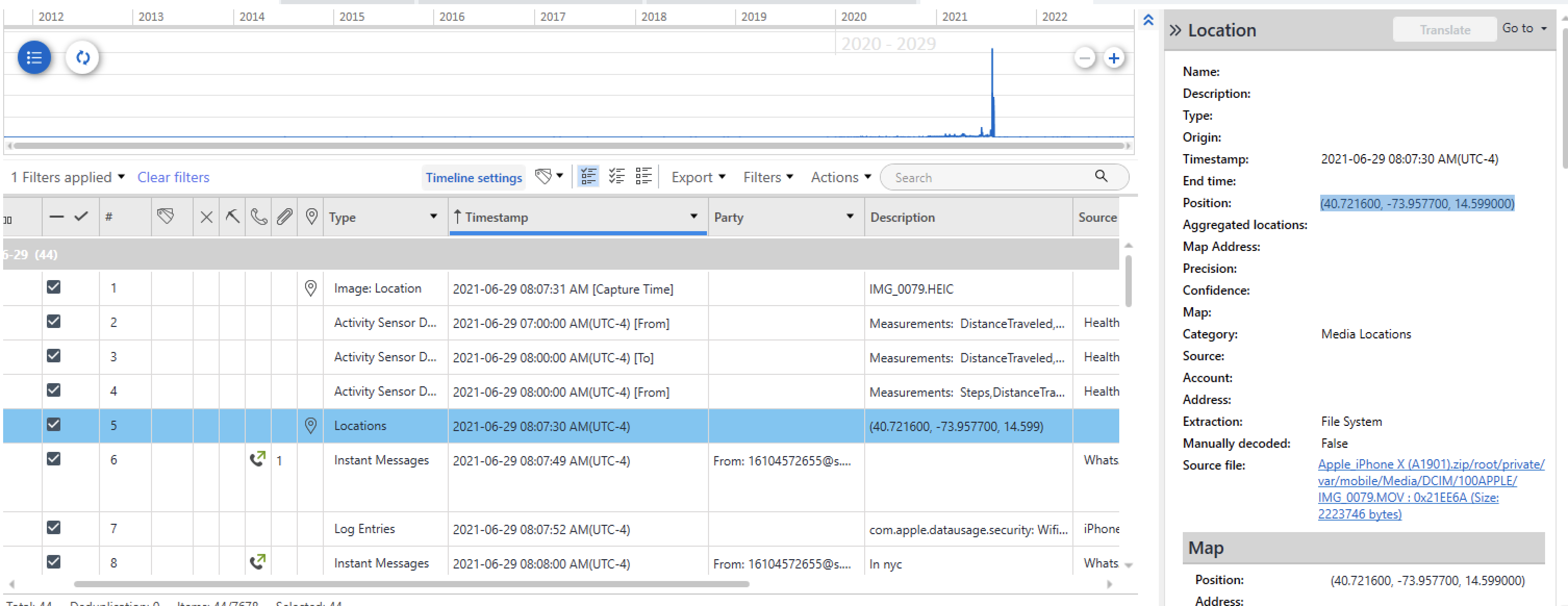
---
Question #33: Two of the suspects use the same app to facilitate money transfers without handling fees. Who are they? Provide first names separated by a comma: [AAA],[BBB]
Flag: Beth,Marsha
This question initially perplexed me. After reviewing all of the images, I discovered that the only Finance-related app shared by two people (Beth and Marsha) was PassBook (Apple Wallet)
---
Question #34: What is the version of the extraction container format in the provided evidence file?
Flag: CLBX-0.3.1
Inside the "Apple_iPhone X (A1901) .zip" archive, containing the forensic acquisition, there is a file called "version" which contains the version of the aforementioned container.
---
Question #36: Who was Beth supposed to meet at the Vienna Inn?
Flag: Heisenberg White
The search term should be simple: VIENNA INN. Looking in PA produced only one result: a chat with Heisenberg White.
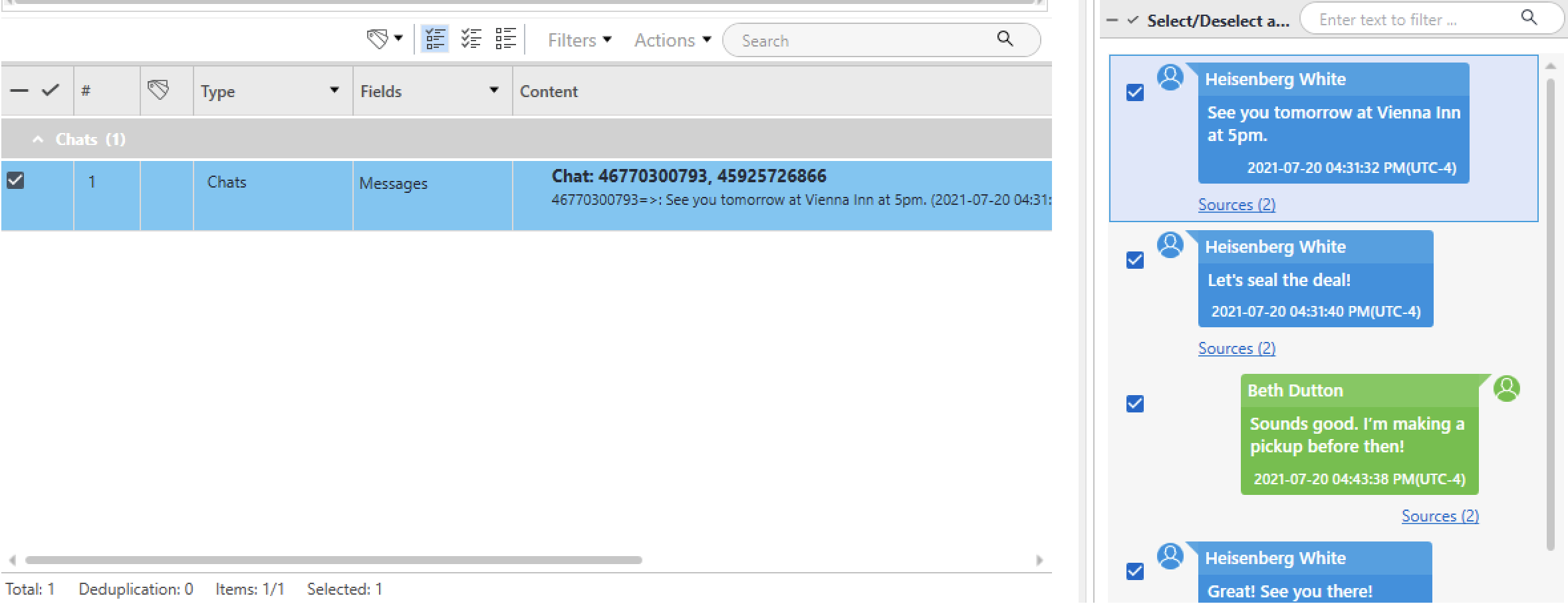
---
Question #37: What was Beth's furthest walking distance?
Flag: 2482.28
The information we require in this case is contained within the "healtdb_secure.sqlite" file. This information is regularly parsed in PA, so in order to answer correctly, sort the "Distance Traveled" or "Steps" column in descending order.
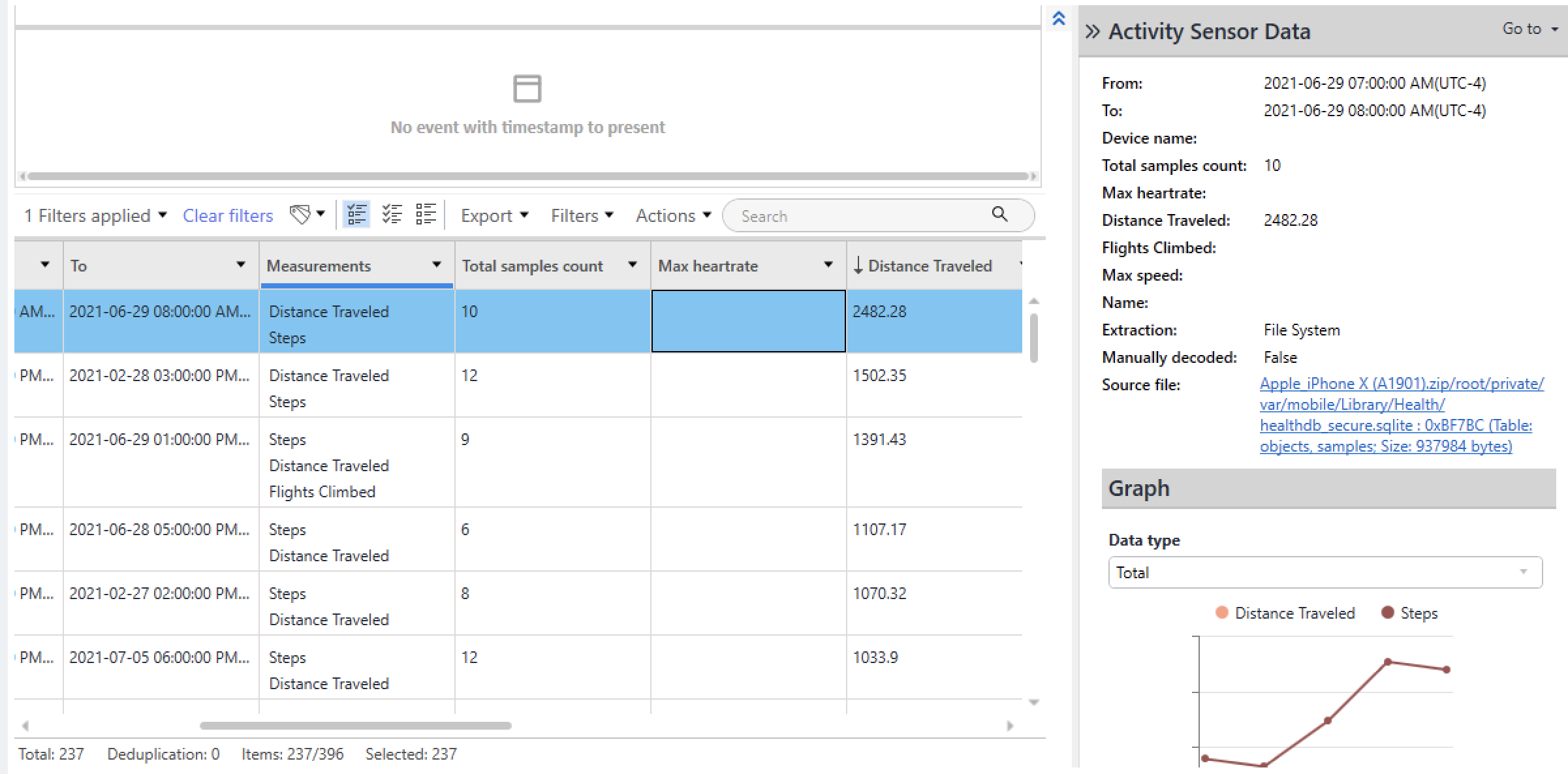
---
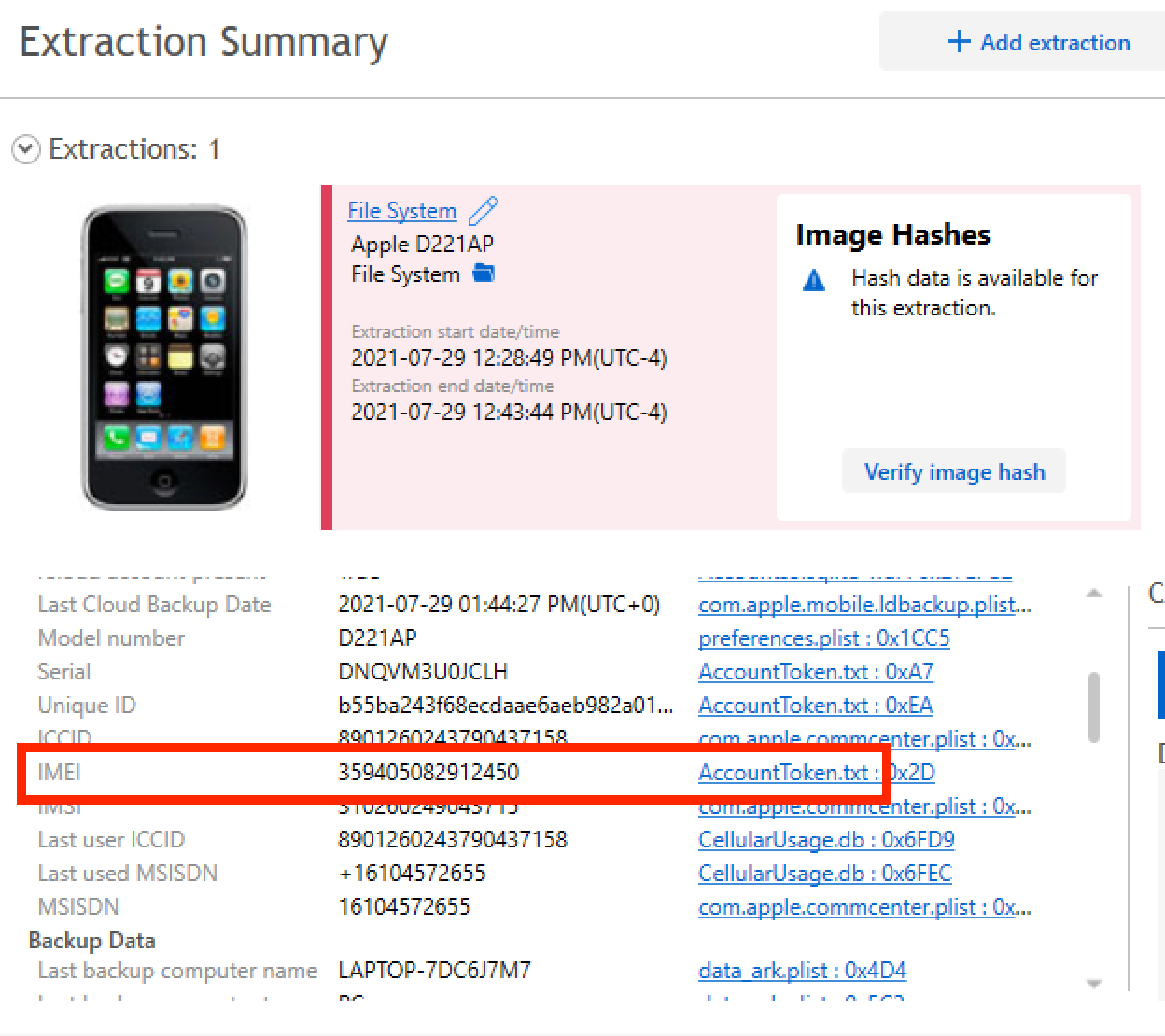
Question #38: What is the IMEI number of the device?
Flag: 359405082912450
From Extraction Summary:
---
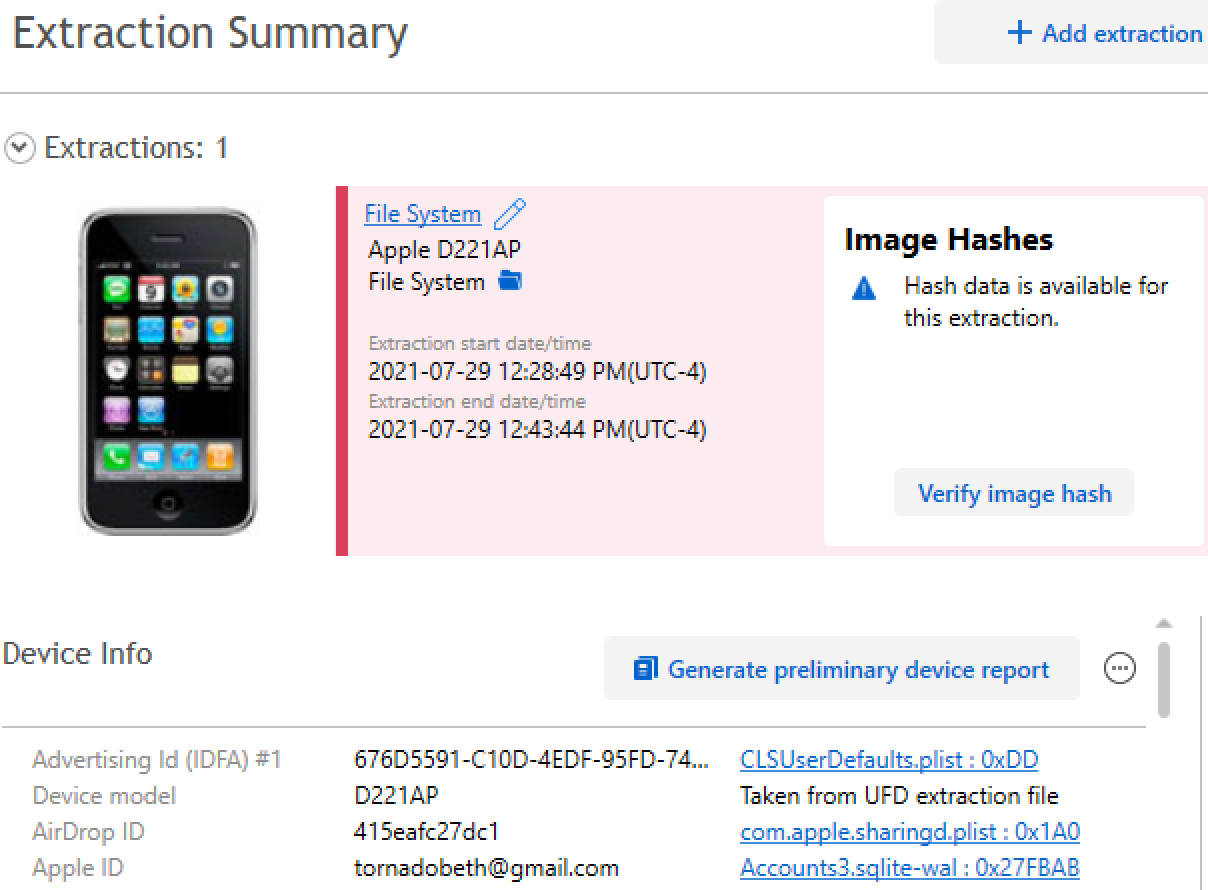
Question #39: What is the Apple ID associated with the device?
Flag: tornadobeth@gmail.com
Again, from Extraction Summary:
---
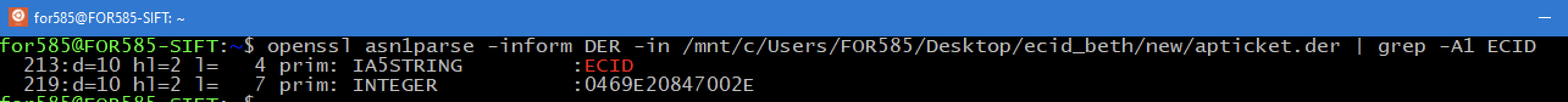
Question #42: What is the Exclusive Chip Identification (ECID) of the mobile device?
Flag: (HEX) 0469E20847002E OR (DEC) 1242319429238830
In this case, I most likely overthought. I remembered finding this information in a file called "apticket.der" (Apple_iPhone X (A1901).zip/root/private/preboot/B9B3C3DDB88197293DC3EC712669C7CBC948745D682EACF7FA8583619A3B6FCBA17BBD2D95D7B1BD824EF956EC423A07/System/Library/Caches/apticket.der). So I went in search of it, and once found, I used the openssl utility to collect the information that piqued my interest:
openssl asn1parse -inform DER -in apticket.der | grep -A1 ECID
---
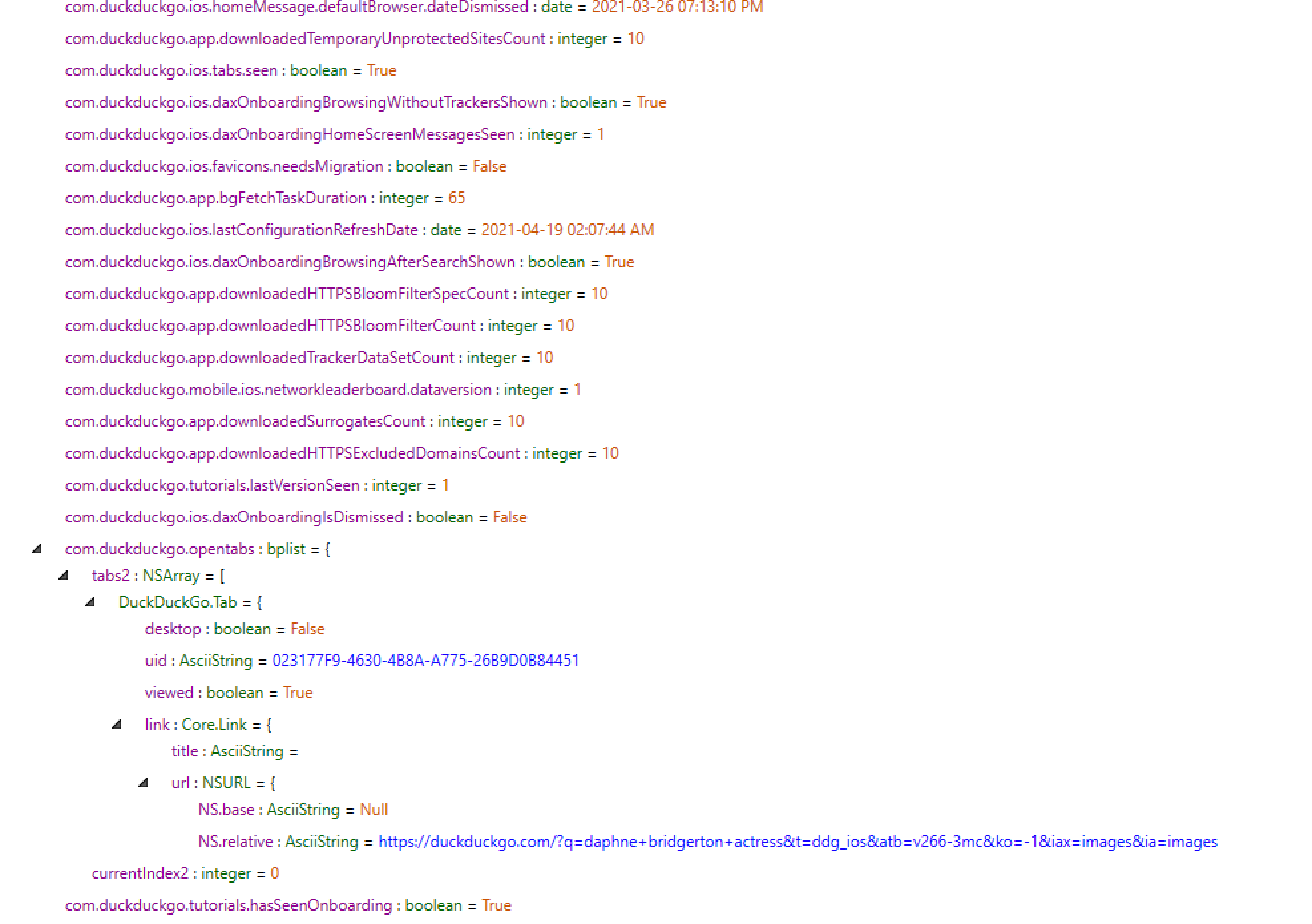
Question #43: What was the search query in the open tab of the DuckDuckGo Privacy Browser?
Flag: daphne bridgerton actress
First off, I looked for any databases that might be linked to DuckDuckGo. To accomplish this, I filtered for the application of interest in PA's "Database" menu:
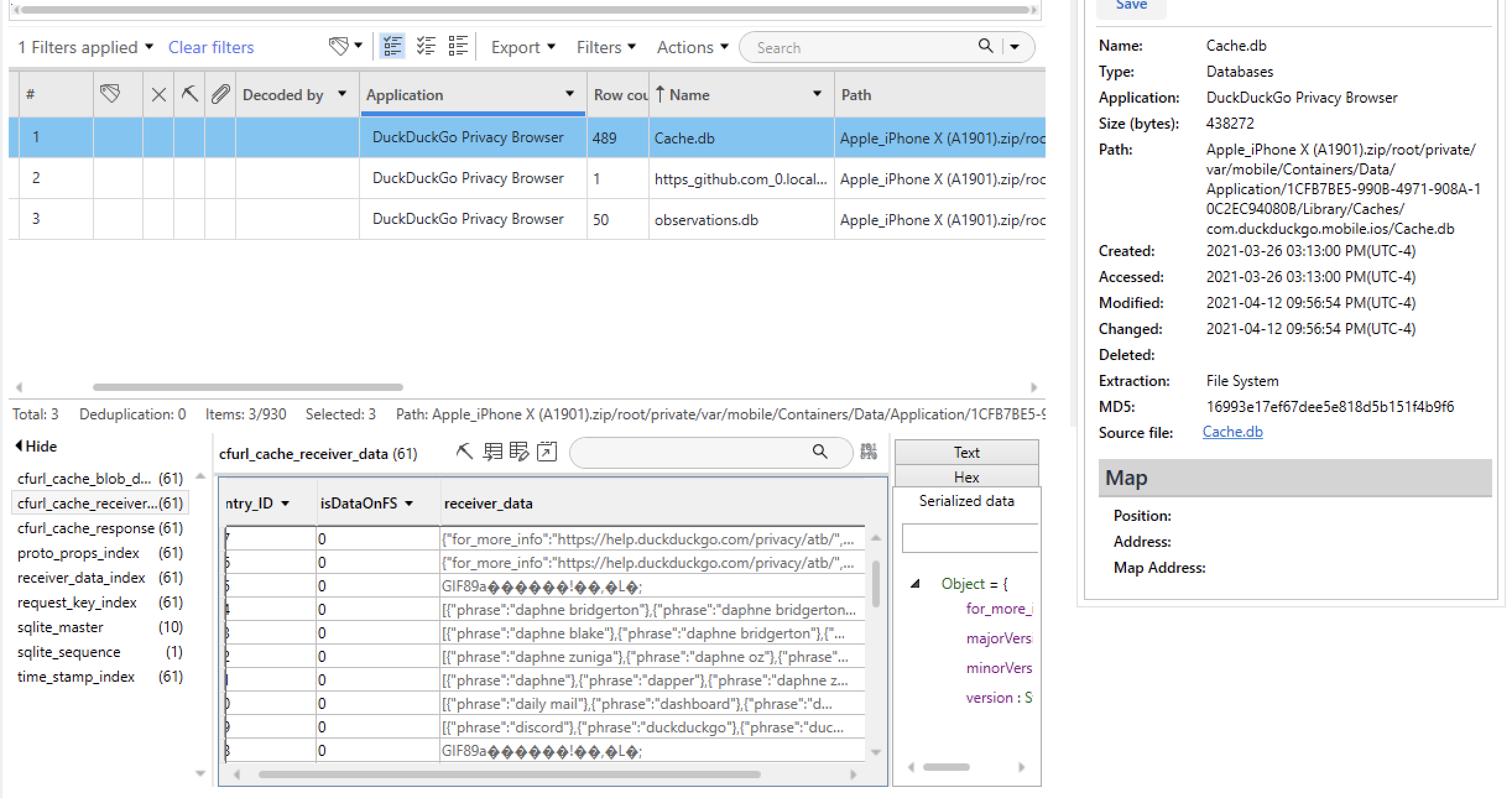
As we can see, the phone user has done a lot of research over time. To answer the question of what the search query in the open tab is, further investigation is required.
A search for the words "duckduckgo" and "plist" yields the file "com.duckduckgo.mobile.ios.plist". We can find the answer to our challenge by looking inside this file (located in /private/var/mobile/Containers/Data/Application/1CFB7BE5–990B-4971–908A-10C2EC94080B/Library/Preferences/).
I hope you found this article useful! Please, feel free to provide any feedback you desire!
See you next year and thanks again Cellebrite!


